
Update 2014-02-06: The SonarQube .NET ReSharper plugin has been released. See my release announcement.
Update - I've moved my plugin into the "SonarQube Forge" and hosting the source, etc, under the SonarCommunity plugins. The information on this page is now stale. See my post SonarQube .Net ReSharper Beta Release for updated information.
I've created a fork of the SonarQube .Net ecosystem plugin's GitHub repository with the purpose of adding a new plugin to support the free JetBrains ReSharper command line code inspection tool. I have full intention of submitting this back to the main SonarQube dotnot plugin repository once it's stabilized, under SONARDOTNT-348.
The fork can be found at (no longer hosted here), if you want to try it yourself. I provide no warranty, no guarantee and limited support (I'm just one guy, doing this in 30-minute chucks on my train ride to/from work). I'm using the LGPL v3 license for this code, same as the .Net ecosystem plugins, so the code is open for anyone -- thus the use of GitHub. You are free to modify it yourself, in accordance with the license, and I will accept pull request, should you wish to provide them.
Currently, this plugin only support reusing an existing report, although I will be adding support to run the analysis directly in the next month or so.
Installation Instructions:
Install .NET plugins 2.2-SNAPSHOT
This plugin requires you use the "2.2-SNAPSHOT" builds of the C#/.NET plugins for SonarQube. While you can build these from within my fork, since I'm not actively integrating upstream changes, I suggest you don't use these and pull from the official sources. I will provide some support for the ReSharper plugin, but for the rest of the .NET Ecosystem plugins you should go through the upstream maintainers.
Install ReSharper Command Line Tools and Analyze
To use the new sonar-dotnet-resharper-plugin, you'll need to download the ReSharper command line tools from JetBrains and use the inspectcode.exe utility to analyse your solution. There are several command line options for the tool, but at minimum, you'll need this:
inspectcode.exe -o=resharper-results.xml YourSolutionName.sln
Where -o=resharper-results.xml will write the results into the file name you provide. Note: by default (without the -o argument), inspectcode will write the file to the temp directory. You'll need this file to provide to my SonarQube plugin.
You can also optionally provide the name of a single project in the solution to limit the analysis to just that project.
Install My Plugin
Install the sonar-dotnet-resharper-plugin into your SonarQube server's \extensions\plugins folder and restart the SonarQube server. In the server's log file, you should see lines like this:
2013.09.12 22:22:08 INFO org.sonar.INFO Register rules [resharper-cs/cs]...
2013.09.12 22:22:09 INFO org.sonar.INFO Register rules [resharper-cs/cs] done: 718 ms
2013.09.12 22:22:09 INFO org.sonar.INFO Register rules [resharper-vbnet/vbnet]...
2013.09.12 22:22:09 INFO org.sonar.INFO Register rules [resharper-vbnet/vbnet] done: 313 ms
Now, add the following to your sonar-project.properties file(s):
#ReSharper
sonar.resharper.mode=reuseReport
sonar.resharper.reports.path=resharper-results.xml
Where the value of sonar.resharper.reports.path is the path to the ReSharper results file relative to each project file. This has the current limitation (same as the FxCop and other sonar-dotnet plugins) of requiring the same relative path be used for all projects. As such, if your filesystem layout has project files at different depths relative to the results file, you will have to copy the results file to each project's folder so that the relative path works.
Right now, for sonar.resharper.mode it only supports reuseReport. In the (near) future I will add the ability to directly run project-level ReSharper analysis instead of reusing a report, which will work much better for people that have differing depth project files.
Modify Your Project's Quality Profile
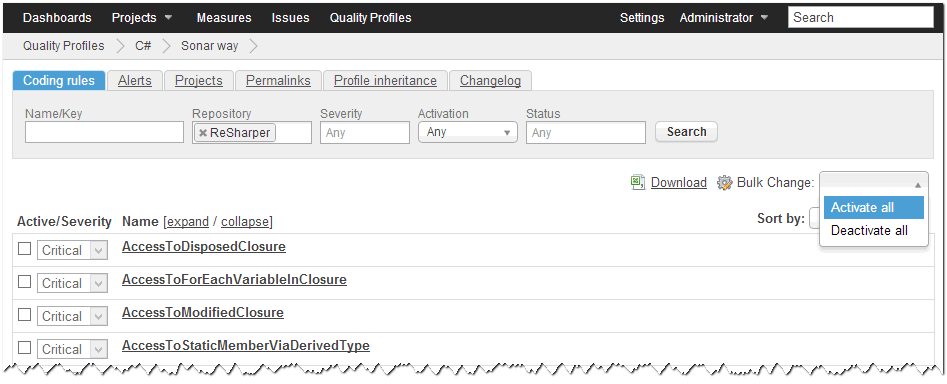
If you install the sonar-dotnet-resharper-plugin on a clean system where you have not modified the "Sonar way" Quality Profile, then all of the new ReSharper-based rules will be included and enabled immediately. However, if you have modified that profile or have your own custom profile(s), you will need to enable the ReSharper rules for that profile. To do this, go into the SonarQube web UI, click the "Quality Profiles" link in the header bar, and choose the profile you wish to include ReSharper results.
In the filter boxes, choose "ReSharper" in the Repository field and "Any" from the Activation field and submit. I expect you'll see a list of approx 240 rules, all disabled. In the upper right corner of the results list is a "Bulk Change" option. Choose "Activate all". This will (immediately) activate all of the ReSharper rules for this profile.
A Note About Rule Severity
ReSharper users a four-tier severity, while SonarQube uses a five-tier system. I have mapped the ReSharper values like this:
| ReSharper | SonarQube |
|---|---|
| Error | Blocker |
| Warning | Critical |
| Major | |
| Suggestion | Minor |
| Hint | Info |
Note that there is no mapping to the SonarQube 'Major' category, but this is the fall-back/default value SonarUses for a rule, so if you see any (or all) of the ReSharper rules in this tier, please let me know -- there was likely an error importing the rules into your SonarQube installation.
You can, of course, change these levels for any rule using the Quality Profile, and I fully expect most people will want to downgrade a lot of the 'Critical' rules to 'Major'.
Run the sonar-runner!
Now run sonar-runner on your SonarQube project. You should now see your new ReSharper violations in the SonarQube web reports.
Current limitations
SonarQube requires that the rule database be populated up front, at server start. However, ReSharper does not (yet) publish a list of possible violation types for their tool, so the rules in the plugin are only those which I've come across so far in my own C# projects. This means that it's possible, likely even, that you will have violations in your code that the plugin does not know about, so cannot import into SonarQube appropriately. When the plugin comes across one of these, it will write a log statement (to the runner's log). In a future release, it log more information on how to 1) submit that rule back to me for inclusion in a future plugin build and 2) add it to a local supplement file for inclusion in your local rules. For now, if you hit this, you can email me with the block of your ReSharper results block and I'll update the plugin. Also, I have an open request with JetBrains to provide a mechanism to get the full list of violations up front so that this issue will be less likely going forward.
The sonar-dotnet API does not currently work for .xaml files, so any violations in .xaml files are not reported in SonarQube.